
The MUHC has various policies on information security that includes:
- Information security,
- Confidentiality and Privacy,
- Use of wireless devices,
- Use of social media,
- Use of the cloud,
- Photo policy
This to ensure an overall protection of MUHC informational assets in order to prevent risks that may compromise the confidentiality, integrity and availability of MUHC informational assets.
Here are some basic principles that help us achieve patient’s security and privacy.
Confidentiality: the nondisclosure of information except to an authorized person.
Integrity: ensuring that information and data are unimpaired, sound and whole or complete.
Availability: ensuring systems’ services and data are accessible, on demand, by authorized entities.
When navigating on the internet/intranet or using MUHC assets during your stage, keep in mind that unauthorized use of copyrighted material, publishing, downloading or transmitting threatening or obscene material, use for commercial activities, product advertisement or political lobbying and use of vulgar or obscene language are all prohibited.
The documents below will help you understand the issues that come from improper use or conduct around MUHC informational assets or that of staff personal devices.
Check out these short vignettes. (1 minute) (5 of them)
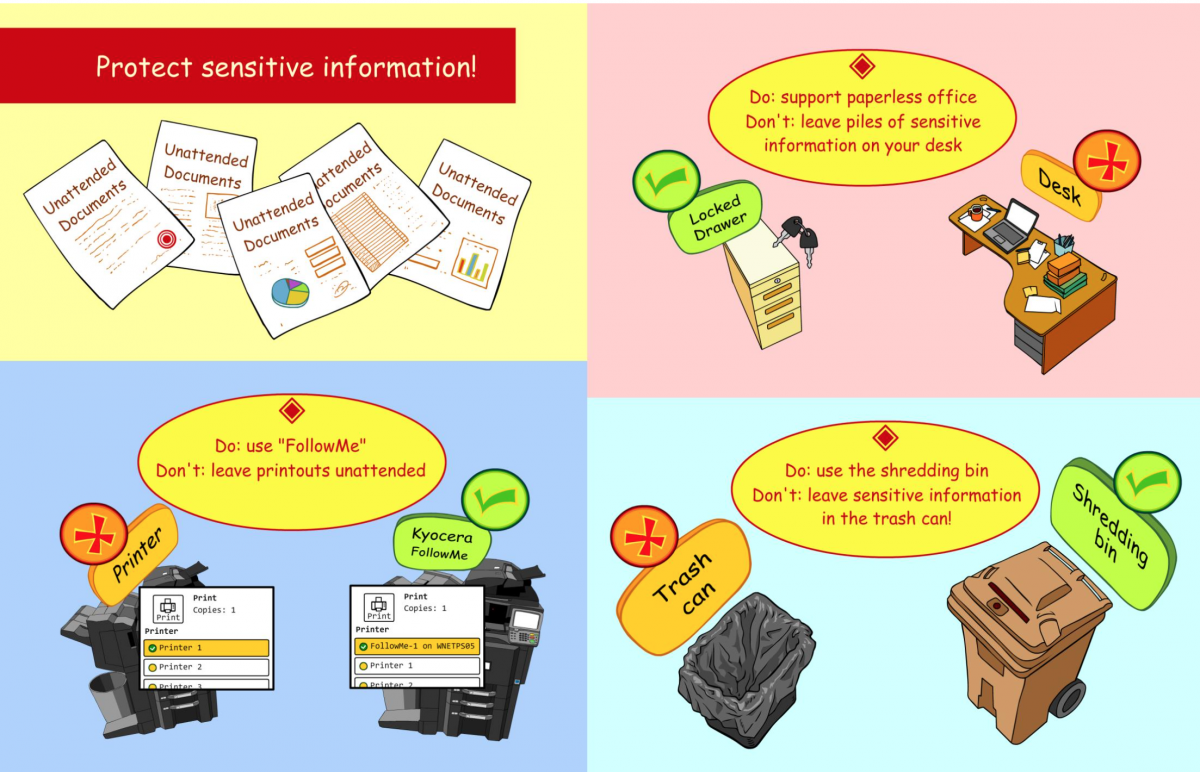
Protect sensitive information! (Poster)
Understanding your Role
To help you understand your role and your responsibility with respect to security and confidentiality, we propose the following topics and resources:
- Learn more about the components of our Security Program, your role and your responsibilities
- Beware of common security risks: Identity theft and other exploits
- Wireless devices
- The use of wireless telecommunication devices (phones, tablets, computers) is permitted on all MUHC sites, unless otherwise specified in designated areas as indicated visibly by explicit signature. However, make sure you :
- Limit your use to a minimum when within the MUHC walls
- Avoid use for personal matters
- Put your device in “vibration” mode
- Use it in an appropriate space to avoid inconveniencing others
- Use a low tone and respectful language
- Respect information confidentiality
- Do not use the camera or video within the MUHC
- The use of wireless telecommunication devices (phones, tablets, computers) is permitted on all MUHC sites, unless otherwise specified in designated areas as indicated visibly by explicit signature. However, make sure you :
- Cloud
- The use of cloud is prohibited in certain occasions (Dropbox, OneDrive). Please refer to MUHC policies
- Social media
- Social Media plays an increasingly larger role in communication and self-expression, including new opportunities for communicating with patients and/or their families, third persons, or other team members. Be reminded that what is published on social media may be widely accessible and may be around for a long time online. Therefore, make sure you follow these simple rules when using social media:
- Consider carefully the content of what you post
- Respect patient confidentiality (do not share patient name, photos or videos, medical details even if patient’s name is not disclosed)
- Do not provide any medical advice
- Do not publish, post or share malicious, threatening, offensive or discriminatory statements
- Avoid posting negative comments or derogatory statements that could cause harm to the reputation of the MUHC or the personnel and professionals
- Avoid recommending any particular treatment, product or services unless explicitly authorized by the MUHC
- Social Media plays an increasingly larger role in communication and self-expression, including new opportunities for communicating with patients and/or their families, third persons, or other team members. Be reminded that what is published on social media may be widely accessible and may be around for a long time online. Therefore, make sure you follow these simple rules when using social media:
- Photo
- Don’t take pictures without patient consent
- Avoid using your devices for photos/videos for unnecessary reasons
Components of Security Program
 The MUHC Security and Confidentiality Program
The MUHC Security and Confidentiality Program
Most security related problems involve, or are caused by, our own behavior and that of people like us. Most of the solutions to these problems are found when we modify our behavior.
Each of us must understand that the information that we gather and store about individuals or organizations belongs to them and is to be held in a trust. Subsequent holders of the information are also bound by this trust. If we guard this trust and let our behavior be directed by it, many potential security related problems can and will be avoided.
Administrative and organisational responsibilities
The MUHC Board, the Information Services Steering Committee, the Security and Confidentiality Committee, the IS Security Committee and the Security & Confidentiality Co-ordinator are working in concert to ensure the development and implementation of Policies & Procedures related to the security and confidentiality of the MUHC's informational assets.
Personnel responsibility
It is each individual's responsibility to make themselves aware of the MUHC Policies and Procedures related to security and confidentiality of informational assets and to respect them by implementing them in their daily work environment. The "acceptable use of informational assets" policy describes the terms of responsible use of the assets currently in place.
Physical security
Physical security involves safeguards against loss of assets such as computers, servers, telecommunication material and its environment due to physical damage or environmental hazards. Picture ID cards for all MUHC members, dedicated rooms located in properly secured areas, strict access control mechanisms, and inventories of informational assets in place and in circulation are concrete measures to ensure physical security of MUHC assets.
Information Management security
The security measures related to the management of information encompasses the functionality and procedures related to the access, acquisition, analysis, storage, use, evaluation, transmission, backup and destruction of information required to fulfil the MUHC mandate. These procedures are developed in consideration of the sensitivity of the data. The security measures imply the management of confidential information and/or nominative data as per the laws and regulations, which the MUHC must respect: The «Law on Access » (A2.1), takes into account the collection and the transmission of nominative information as well as the obligation to obtain consent and authorisation from patients (or representative) in clearly indicated situations. The "commission d\'accès à l\'information" (CAI) published clear directives related to the management of electronic files containing confidential information. Risk management, incident reporting specific to the informational assets and the management of confidentiality agreement with other agencies are also security measures.
Information Technology security
The use and access to informational assets by an individual must be in relation to his or her role within the MUHC, supporting its mission and being duly authorised. The MUHC informational assets must be protected by security measures that would ensure prevention and detection of malicious attack, the development and communication of contingency plan in case of system failure and the updated disaster recovery plan. Documentation on the latter will be available on the Intranet shortly.
To report an incident related to security and/or confidentiality of electronic informational assets, call the Service Desk 48484. They will direct your call to the appropriate personnel.
Identity and Data

Phishing:
Risk: User identity theft, or defraud / Confidentiality-Integrity
In computing, phishing is a criminal activity using social engineering techniques. Phishers attempt to fraudulently acquire sensitive information, such as passwords and credit card details, by masquerading as a trustworthy person or business in an electronic communication. Phishing is typically carried out using email or an instant message, although phone contact has been used as well.
Malware:
Risk: Impact on Integrity, Availability, Confidentiality
Malware or Malicious Software is software designed to infiltrate or damage a computer system without the owner's informed consent. It is fusion of the words "malicious" and "software". The expression is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software or program code. It includes computer viruses, worms, trojan horses, spyware, adware, and other malicious and unwanted software.
Spyware:
Risk: User identity theft, defraud / Confidentiality
Spyware is computer software that collects personal information about users without their informed consent. Personal information is secretly recorded with a variety of techniques, including logging keystrokes, recording Internet web browsing history, and scanning documents on the computer's hard disk. Purposes range from overtly criminal (theft of passwords and financial details) to the merely annoying (recording Internet search history for targeted advertising, while consuming computer resources).
Trojan Horse:
Risk: Affect networks, systems, files / Integrity and Availability
In the context of computer software, a Trojan horse is a malicious program that is disguised as or embedded within legitimate software. They may look useful or interesting (or at the very least harmless) to an unsuspecting user, but are actually harmful when executed. There are two common types of Trojan horses. One, is otherwise useful software that has been corrupted by a cracker inserting malicious code that executes while the program is used. Examples include various implementations of weather alerting programs, computer clock setting software, and peer to peer file sharing utilities. The other type is a standalone program that masquerades as something else, like a game or image file, in order to trick the user into some misdirected complicity that is needed to carry out the program's objectives. Trojan horse programs cannot operate autonomously, in contrast to some other types of malware, like viruses or worms. Just as the Greeks needed the Trojans to bring the horse inside for their plan to work, Trojan horse programs depend on actions by the intended victims.
Virus:
Risk: Affect network, files, systems/ Integrity and Availability
A computer virus is a computer program written to alter the way a computer operates, without the permission or knowledge of the user. Though the term is commonly used to refer to a range of malware, a true virus must replicate itself, and must execute itself.
Worm:
Risk: Affect networks / Availability and Integrity
A computer worm is a self-replicating computer program. It uses a network to send copies of itself to other nodes (computer terminals on the network) and it may do so without any user intervention. Unlike a virus, it does not need to attach itself to an existing program. Worms always harm the network (if only by consuming bandwidth), whereas viruses always infect or corrupt files on a targeted computer.
